Our Security Philosophy
Our security strategy is anchored in two core principles: defense in depth and secure by design. As an AI platform that orchestrates model deployments, handles MCP communications, and manages sensitive data flows across your infrastructure, security is not an afterthought—it’s embedded into every layer of our architecture. We believe modern software security requires proactive measures rather than reactive responses. Our approach combines industry-standard security practices with secure defaults and automated tooling to create a robust security posture that scales with your needs.Defense in Depth
Secure by Design
Automated Security
Human Expertise
Beyond Automated Tools: Human-Centered Security
While our automated security tooling provides comprehensive coverage, we recognize that true security requires human expertise and collaborative oversight. Our security posture extends beyond automated scanning:Expert Security Code Reviews
Expert Security Code Reviews
Threat Modeling & Risk Assessment
Threat Modeling & Risk Assessment
Security Architecture Review
Security Architecture Review
Penetration Testing
Penetration Testing
Community-Driven Security
Community-Driven Security
Security Champion Program
Security Champion Program
Comprehensive Security Pipeline
Our security pipeline operates at multiple levels, ensuring that vulnerabilities are caught as early as possible in the development lifecycle:Pre-commit Security Gates
- Static analysis with Bandit for common security issues
- Semantic pattern matching with Semgrep for complex vulnerability patterns
- Secrets detection with Dodgy and Gitleaks for hardcoded credentials
- Type checking and code quality enforcement
Continuous Integration Security
- 30+ security scans trigger automatically on every PR
- CodeQL and Semgrep for deep semantic code analysis
- Gitleaks for comprehensive secret detection across git history
- pip-audit and npm audit for dependency vulnerability scanning
- Container security assessment for all containerized components
Supply Chain Security
- Automated dependency vulnerability scanning
- Software Bill of Materials (SBOM) generation for complete transparency
- License compliance checking to ensure all components meet security standards
- Continuous monitoring of upstream dependencies for new vulnerabilities
Container Security Hardening
- Multi-stage builds to minimize attack surface
- Minimal base images with the latest security updates
- Non-root user execution and read-only filesystems
- Comprehensive scanning with Grype
Runtime Security Monitoring
Compliance Certifications
Truefoundry maintains multiple compliance certifications to meet enterprise security and regulatory requirements:- SOC 2 Type II: Certified for security, availability, processing integrity, confidentiality, and privacy
- GDPR: Compliant with the General Data Protection Regulation for data privacy
- HIPAA: Compliant with Health Insurance Portability and Accountability Act for healthcare data



Our Compliance Certifications
Data Security
- Self-Hosted Deployment
- Managed Deployment
Data Residency and Sovereignty
If you are self-hosting the control-plane, Truefoundry’s architecture ensures that your data remains under your control:- Data Stays in Your Environment: When deployed on your infrastructure, all data, models, and artifacts remain within your cloud account or on-premises environment
- No Data Egress: Deploying on your own infrastructure eliminates data egress costs and ensures data never leaves your environment
Emails of the users logging into the Truefoundry platform
Emails of the users logging into the Truefoundry platform
Usage analytics
Usage analytics
- The number of clusters connected to the control-plane
- The addons installed in each of the clusters along with their versions
- The version of the control-plane
- The number of requests flowing through the gateway (Will be enabled in future)
Public Pricing of instance types and models
Public Pricing of instance types and models
Crash and Error Logs
Crash and Error Logs
Encryption
- Encryption at Rest: Encrypted at rest using AES-256 encryption
- Encryption in Transit: All network communications use TLS 1.2 or higher to encrypt data in transit
- Secret Management: Integration with cloud-native secret managers (AWS Secrets Manager, Azure Key Vault, GCP Secret Manager) for secure credential storage
Access Control and Authentication
Authentication Methods
Authentication Methods
- Single Sign-On (SSO): Integrate with your identity provider (IdP) including SAML 2.0 and OIDC-compatible providers like Google, Microsoft Entra ID, Keycloak, Okta, etc. Learn more about our SSO documentation.
- JWT Token Authentication: API access using JWT tokens from your identity provider
- API Keys: Secure API key-based authentication for programmatic access
- Token Rotation: Truefoundry supports automated token rotation for the API keys and tokens used to authenticate with the Truefoundry platform. Learn more about our Token Rotation documentation.
Authorization and Access Control
Authorization and Access Control
Infrastructure Security
Architecture Security
Architecture Security
- The compute plane runs entirely within your Kubernetes cluster (EKS, GKE, AKS, OpenShift, or on-premises). Truefoundry does not provide or access compute resources directly—all workloads execute in your controlled environment
- Your models, datasets, and artifacts stay within your cloud account or on-premises infrastructure, eliminating data egress risks
- The computeplane load balancer can be put behing a private endpoint limiting all external access to the compute plane.
- The compute plane doesn’t require any ingress from the control-plane. Its the compute plane that intiates the connection to the control-plane. The
tfy-agentconnects to the control plane via outbound-only secure WebSocket connections, meaning no inbound ports need to be opened in your firewall - ControlPlane can be selfhosted within your VPC in our enterprise plan.
Network Security
Network Security
- Private Network Deployment: Deploy control plane within your VPC for complete network isolation
- TLS/SSL Encryption: All API communications encrypted with TLS 1.2+
- Firewall Integration: Compatible with your existing firewall and network security policies
- VPC Isolation: Support for deployment within private VPCs and on-premises networks
Container Security
Container Security
- Image Scanning: Integration with container registries and security scanning tools
- Least Privilege: Containers run with minimal required permissions
- Security Contexts: Kubernetes security contexts for pod-level security controls
- Secret Injection: Secure environment variable and secret management without exposing credentials
Audit and Monitoring
Audit Logging
Audit Logging
- Complete Activity History: All user actions, resource changes, and API calls are logged
- Detailed Audit Trails: Track who performed what action, when, and on which resource
- Export Capabilities: Export audit logs to your logging platform (Splunk, Datadog, etc.)
- API Access: Programmatic access to audit logs via Truefoundry API
Security Monitoring
Security Monitoring
- Self-Hosted Deployment
- Managed Deployment
AI Gateway Security
Gateway Security Features
Truefoundry’s AI Gateway provides enterprise-grade security for LLM access:- Authentication: Multiple authentication methods including OIDC, JWT, and API keys
- Authorization: Role-based access control for models and endpoints
- Guardrails Integration: Support for content safety, PII detection, and prompt injection prevention
- Request/Response Logging: Secure logging of API requests and responses for compliance and debugging
Content Safety
Integration with enterprise guardrail providers:- Content Filtering: Azure AI Content Safety, OpenAI Moderation, and custom guardrails
- PII Detection and Redaction: Automatic detection and redaction of personally identifiable information
- Prompt Injection Prevention: Protection against prompt injection attacks
- Toxicity Detection: Real-time detection of harmful or inappropriate content
Incident Response and Business Continuity
High Availability
High Availability
- Globally Distributed: Gateway deployed across 12+ regions and multiple cloud providers including AWS, GCP and Azure.
- Automated Failover: Automatic routing to healthy regions in case of regional downtime
- Multi-Cloud Multi-region deployment of control-plane: Control-Plane is deployed across three regions and three cloud providers in active passive mode and has disaster recovery enabled.
- Redundancy: High availability configurations for critical components
Disaster Recovery
Disaster Recovery
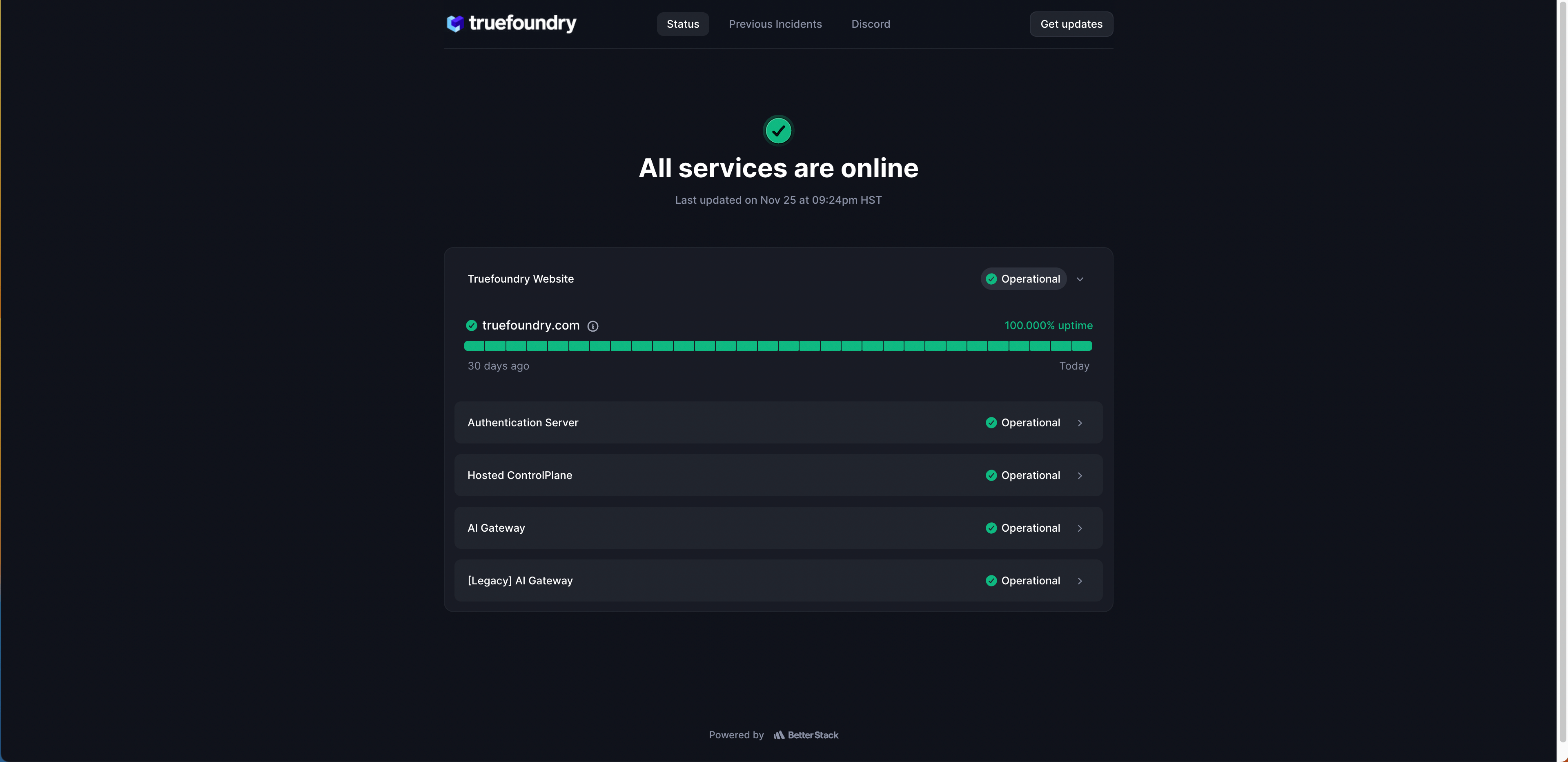
Status Monitoring
Status Monitoring
Backup and Recovery
Backup and Recovery
- Configuration Backups: Regular backups of platform configuration and metadata
- Disaster Recovery: Comprehensive disaster recovery procedures
- Data Backup: Integration with your backup solutions for data plane storage
- Recovery Procedures: Documented procedures for rapid recovery from incidents
Vulnerability Management, Logging and Monitoring
- Self-Hosted Deployment
- Managed Deployment
- A regular vulnerability scanning program in place to ensure that security issues are identified and remediated promptly, as outlined in the Technical Vulnerability Management section of the Operations Security Policy.
- There is auditing and logging enabled across the systems and network devices to maintain visibility into system activity. AWS CloudTrail is integrated with CloudWatch as a centralized logging and monitoring solution. This setup correlates events and generates alerts for our team whenever a potential security incident is detected.
- Additionally, 24/7 monitoring of security alerts is maintained through this system to ensure continuous oversight and rapid response.
Security Reporting
Vulnerability Reporting
Vulnerability Reporting
- Security Contact: Report vulnerabilities to security@truefoundry.com
- Responsible Disclosure: We follow responsible disclosure practices
- Response Time: We aim to respond to security reports within 48 hours
Security Updates
Security Updates
- Security Advisories: Published on trust.truefoundry.com
- Release Notes: Security updates included in platform release notes
- Notifications: Security-critical updates communicated to customers
Data Privacy
Privacy Controls
Privacy Controls
- Data Minimization: Only collect and process data necessary for platform operation
- User Data Control: Users can manage their own data and access permissions
- Data Retention: Configurable data retention policies
- Right to Deletion: Support for data deletion requests in compliance with privacy regulations
GDPR Compliance
GDPR Compliance
- Data Subject Rights: Support for data access, rectification, and deletion requests
- Privacy by Design: Privacy considerations built into platform architecture
- Data Processing Agreements: Standard data processing agreements available
- Privacy Policy: Comprehensive privacy policy available on our website
Third-Party Security
Vendor Security
Vendor Security
- Security Assessments: Regular security assessments of third-party vendors and integrations
- Secure Integrations: All integrations use secure authentication and encryption
- Vendor Monitoring: Continuous monitoring of vendor security practices
Integration Security
Integration Security
- OAuth 2.0: Secure OAuth-based integrations with cloud providers
- API Security: All API integrations use secure authentication methods
- Credential Management: Secure storage and rotation of third-party credentials
Security Best Practices - Recommendations for Customers
- Enable SSO: Use single sign-on with your identity provider for centralized authentication
- Implement Least Privilege: Grant users only the minimum permissions required for their role
- Regular Access Reviews: Periodically review and audit user access and permissions
- Enable Audit Logging: Monitor audit logs regularly for suspicious activities
- Use Secret Management: Store sensitive credentials in secret managers, not in code
- Network Segmentation: Deploy Truefoundry in isolated network segments when possible
- Regular Updates: Keep Truefoundry components updated to the latest versions
- Enable Guardrails: Use content safety guardrails for AI Gateway deployments
Sub-Processors
- Self-Hosted Deployment
- Managed Deployment
- FusionAuth: Used for authentication
- AWS: Used for hosting, storage and security monitoring
- Sentry: Used for error and crash logs
- Posthog: Used for user event and analytics